The Basic Principles Of Parental Control Software
Wiki Article
The 2-Minute Rule for Vpn Services
Table of ContentsThe Definitive Guide to Internet SafetyAn Unbiased View of Online Identity ProtectionHow Parental Control Software can Save You Time, Stress, and Money.Get This Report about Vpn ServicesThe Basic Principles Of Online Identity Protection 9 Simple Techniques For Online Identity Protection
If we discuss it particularly it's Part 2 of Avoidance of Electronic Crimes Act, 2016, that offers information concerning crimes of computer misuse as well as to bill for the specific criminal offense. Stealing and abuse of personal information. As computer has numerous ways where individuals can take information and abuse it, as computer system is a gadget which is quick as well as procedure any type of task promptly, so when it pertains to the moving or copying data it performs with simplicity and also in seconds.
If some prohibited or uncertified accessibility that has actually been used for hacking objective, where an uncertified person utilizes a computer system, network or the Net to hack the target's system without having any type of type of consent to access and also manage the system. Whenever the system is hacked the target don't understand anything that his/her information has actually been hacked and a lot of the moment hackers do hacking to risk the victim.
That the computer system or any type of system will not be hacked conveniently as their safety and security of accessing system will certainly be high. When a crime is done by a private after that he or she is bound for certain criminal offense then that person is billed with high quantity of money as the fees for underhanded misuse of somebody personal privacy, as well as in some situations, there are imprisonment if the lawbreaker was involved in several crimes.
Get This Report about Online Identity Protection
So, the grown-up child can quickly access. These profane materials have high threat damages the future of young generation, yet the law states it is a criminal activity to produce and also disperse off-color material that is not great for the young people who are listed below age of 18. Basically, the act of significant crimes will be used to provide the penalty to the person who utilizes computer innovation and also the Web to acquire, spread or share/distribute the vulgar material that have repulsive video clips, images.These organizations have actually provided facility to report them online and also via their details get in touch with so that the individual can report about the child sexual assault notify of pictures or videos in a really safety way so the crook can be jailed as well as from the Net to eliminate and clean these sorts of profane things or material.

Excitement About Cybersecurity Training
That triggers significant cash loss to the person. Most of us understand that social websites as well as apps are the sources through which people attach and also share their individual life occasions with buddies, yet because of these situations connected to on-line harassment is raising everyday, where a person utilizes Net solutions to watch on the target while staying confidential and also utilizing public groups or websites to get information about their target.
That cause not only loss of money, but the consumers' trust fund. So, to stop from these type of strikes financial institutions should take security preventative measures as well as safe procedure for the on the internet transactions, to stay secure in future from this kind of accident. There are many laws which supplies security to every individual of the Net from bad guys who utilizes network to hurt the users, but the government needs to take some steps to make entities that instruct the organizations that enforce the regulation, that exactly how to inquiry those crimes which is related to the Web as well as offer in reliable means.
How Online Identity Protection can Save You Time, Stress, and Money.
It is very important Look At This for every Web individual to take the significance about the protection and regulations primarily which manages the criminal activities that are created by the incorrect usage of computer system. And there must be a proper method for the security management to safeguard as well as shield the systems, as well as the particular information inside them.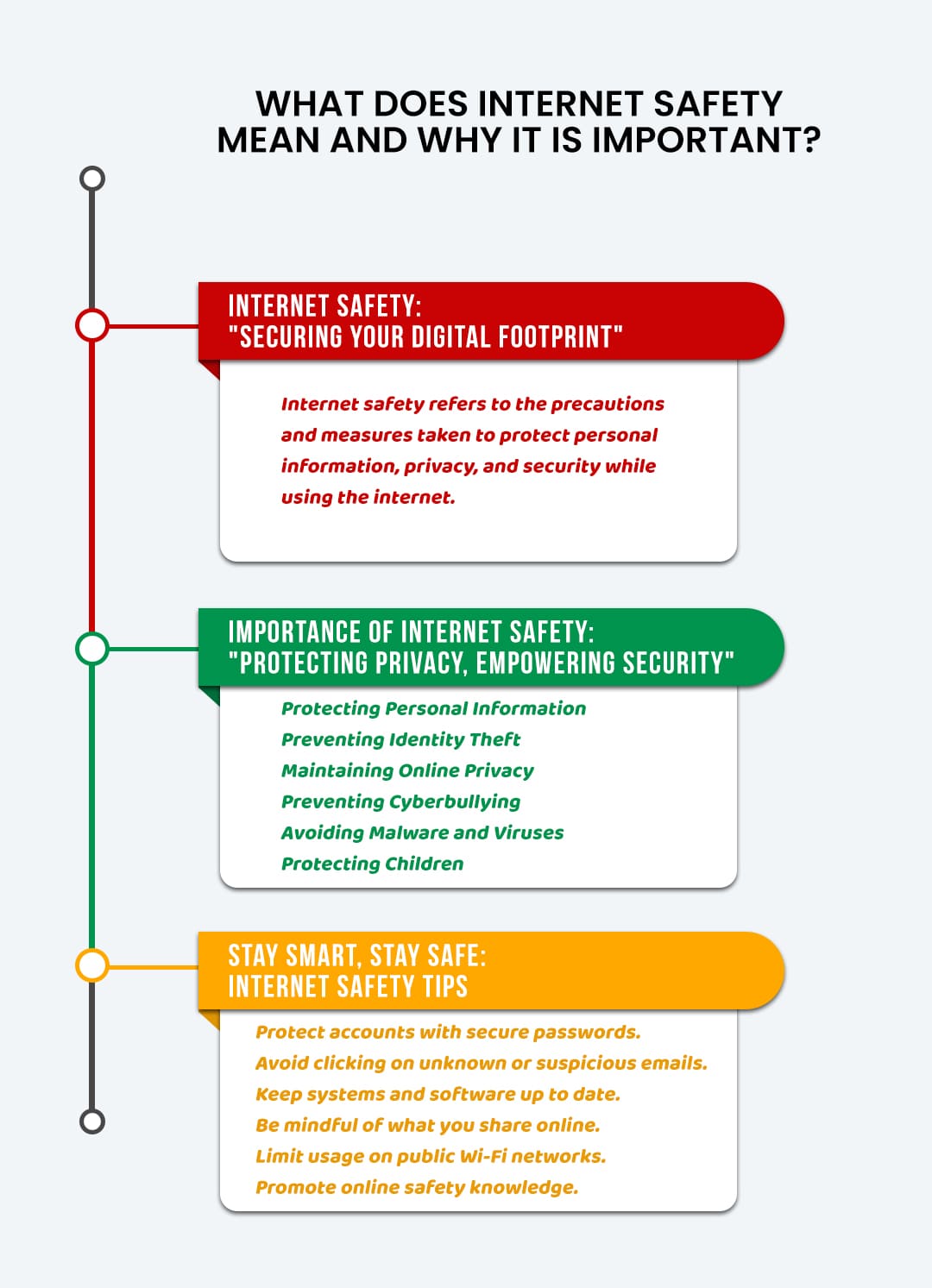
The value of cybersecurity in the electronic globe is immense. As our dependancy on technology expands, so does our vulnerability to these attacks. Cybersecurity helps to secure our data and systems from these threats.
Cybersecurity Training for Dummies
Cyber security is very important for trainees because they typically target virtual assaults. In a recent situation, a group of trainees from an university in the USA was targeted by hackers that got to their individual information, including their Social Safety and security numbers and also charge card info. The cyberpunks then utilized this information to fraudulently charge countless bucks to the students' credit scores cards.This instance highlights the value of cyber safety and security for trainees, who are frequently the victims of cybercrime. If a pupil's personal information is taken in a cyber strike, maybe made use of to dedicate identification theft. It could mess up the pupil's credit rating, making it challenging for the pupil to get fundings for university or a car.
The importance of Cyber Protection for organizations and companies can be seen in the instance of the target data violation. In this instance, cyberpunks were able to acquire access to the target's customer data, consisting of Homepage credit report and debit card info. It resulted in target having to pay out millions of bucks in damages and also shedding consumer count on.
Our Internet Safety PDFs
Another information breach example would certainly be the Wan na, Cry ransomware strike, which targeted businesses and organizations worldwide. This attack led to the loss of information and money for many companies, and some were also compelled to shut down (Internet Safety). licensed Moral Hacking courses for people to work in the direction of protecting information from violations and also malware.If this data had actually fallen under the incorrect hands, it can have been utilized for identity burglary, fraudulence, or various other harmful functions. Recently, there have been several high-profile cyberattacks that have actually had a damaging influence on organizations and also people. Online identity protection. These are theft of social safety and security numbers, financial institution account details, credit card info, and also delicate data leaks
Report this wiki page